Hacking into my dlink router
My ISP has me on a DHCP network and so I don't have a fixed IP address — it keeps changing.
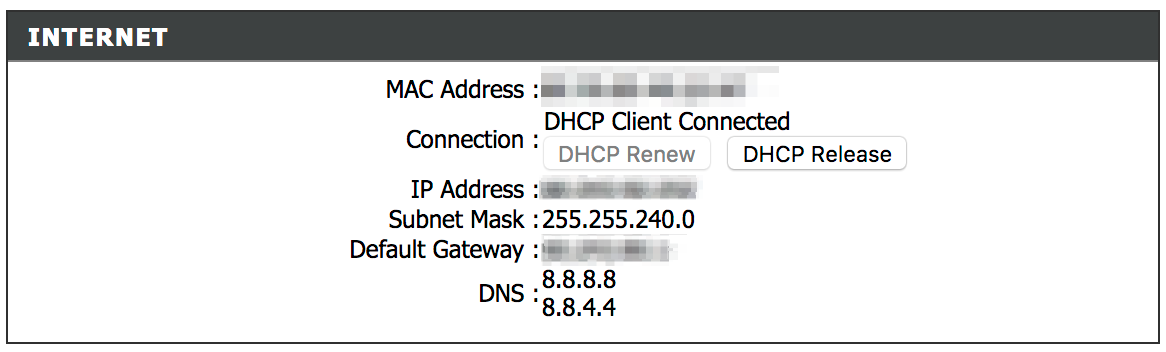
The internet, however, occasionally stops working and I need to log into my router's admin panel and perform a DHCP release+renew to fix it. I don't generally mind it since I can get the internet working without having to call my ISP up. However this happened multiple times a few days back, and it got so annoying that I decided to automate the whole thing.
The CLI
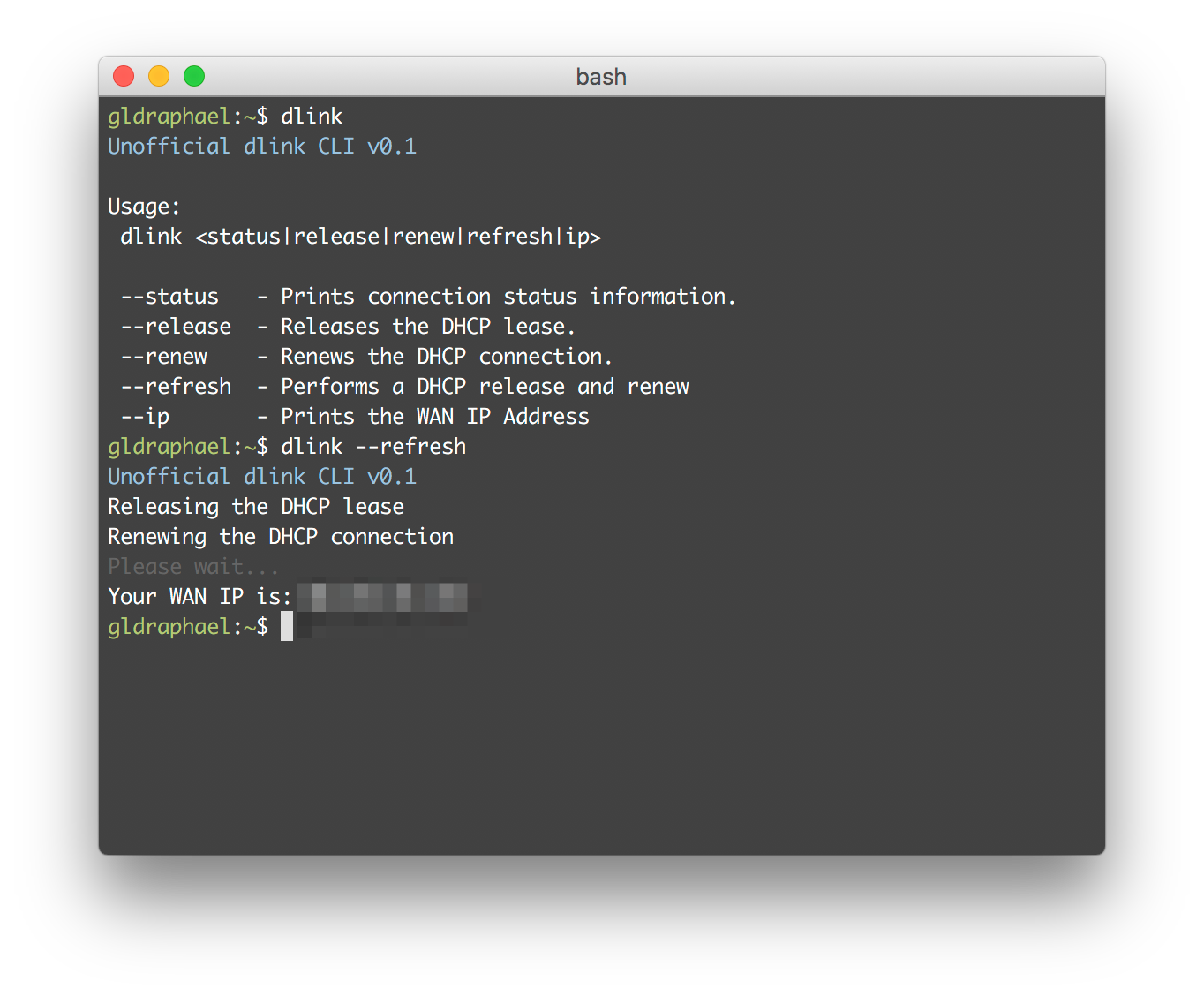
I wanted a command line tool with which I could issue a command to release and renew the DHCP connection. Making the CLI was super easy once I figured out the requests I need to send to the router.
It's a .NET Core Console application which you can get from here.[1]
Observations
The starting point was to inspect the HTTP requests being made while performing the actions needed to do a DHCP release+renew. And here's what I found:
- All requests are
GETrequests. NoPOSTs at all - not even while logging in. - No session management. Once I log into the router, it appends a time based token to the query string which is used to authorize my access. Since the token is time-based, it expires and logs me out after sometime. However, while it's still valid, I could send the URL to anyone in the network and he'll be able to access the admin panel even without knowing the credentials.
- Tokens are only needed to access the pages in the admin panel. The actual requests for releasing and renewing the DHCP lease don't require it.
The third point was the most disturbing finding for me. Because it means that anyone connected to my WiFi router can play games with my router. Could be worse. A malicious site could send potentially dangerous requests to my router!
The WiFi password and trust
This got me thinking about trust. I generally trust people with my WiFi password. But that's all they need to mess around with the network.[2] The admin panel has only been giving me a false sense of security (as far as this router is concerned).
Troy Hunt has an amazing post titled "no, you can't join my wifi network". And you know what? He's right. We shouldn't be sharing our WiFi passwords! Some malicious site could be messing around with the router!

Sorry. I can't be your true friend.
Conclusion
I've been taking routers for granted so far and just stuck with what worked all this while. Time to change that.
And I'm going to change my router at the earliest... which will kind of render my CLI useless... so back to square one!
Github Source: https://github.com/gldraphael/dlink-cli ↩︎
Not that they'll mess around, but the sites they access or the apps they use can do it without their knowledge. ↩︎